Basic Malware RE

Goto Lab
HAPPY NEW YEAR 2025.
This is a new concept for me. Let’s understand how actually the exe works. I am going to mention the every step that I have done to achieve the output. As I said, this is a new topic for me so let’s go step by step.
First Sample
Let’s understand what actually a sample is:
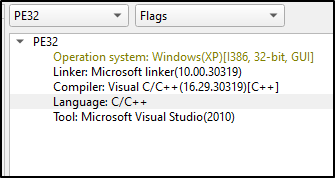
This linker exe is written in C/C++ language. Furthermore, analyzing the entropy we can understand that its not packed.
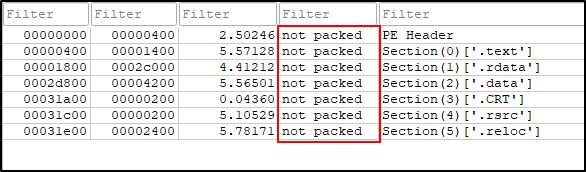
Without any delay let’s just look into the strings.
This is what fucked up looks like 🤣🤣.
But without further ado, lets look out for the best tool IDA to just understand the workflow of this exe. But guess what😁
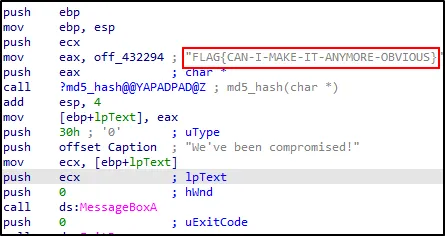
1. What is the flag of which that MD5 gets generated?
FLAG{CAN-I-MAKE-IT-ANYMORE-OBVIOUS}
Second Sample
The first sample is like, THM playing with us. Let’s look into the another sample.
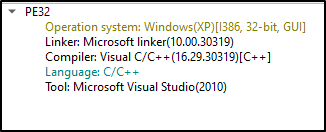
On further analysis, I find it not packed executable:
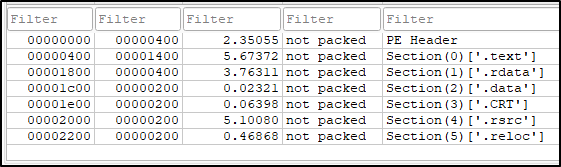
As like before, lets dive what will strings gives us:
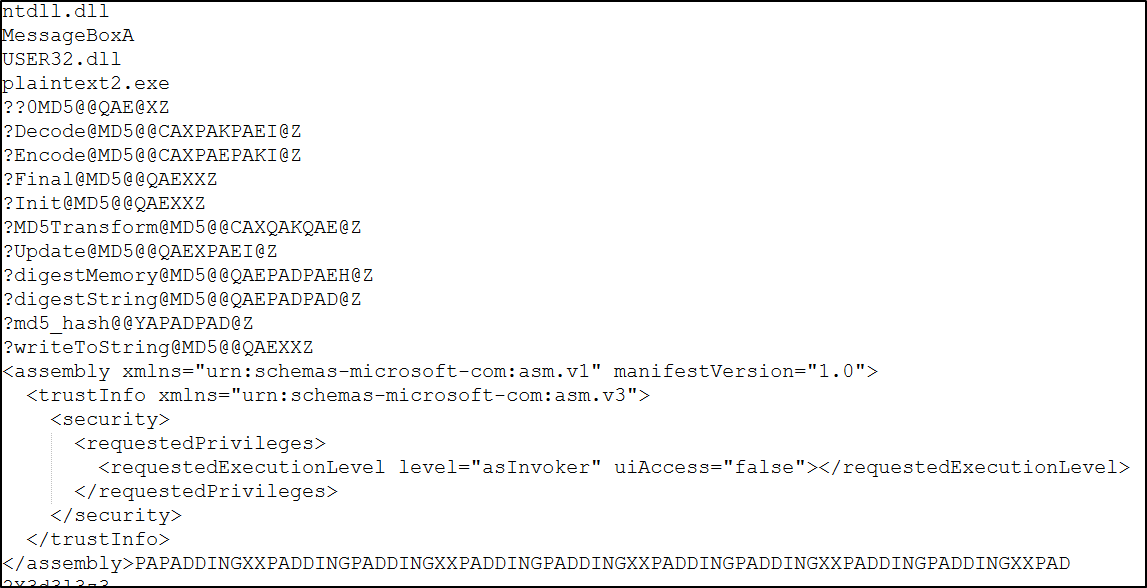
And similarly when we open the executable using IDA we got something:
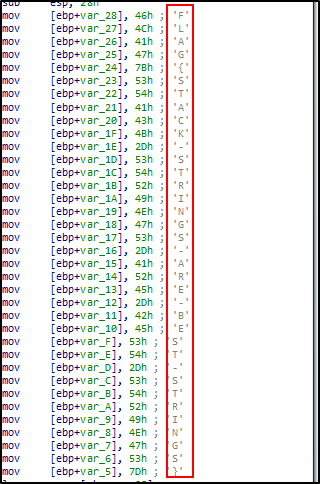
2. What is the flag of which that MD5 gets generated?
FLAG{STACK-STRINGS-ARE-BEST-STRINGS}
Third Sample
I dont like the way they are just giving us the flag in the hand. It also could be the other way to find the flag. But as they said, we are not using and xdbg right now.
As like before lets analyze the third sample
I have looked similarly for the strings. It was the same output file like before. But this time when i looked into our tool IDA it was not just displaying the flag for us. This is now interesting 😁. Let’s decompile the executable. In this case i used the help of Ghidra, and following the entry function I found something interesting 😁
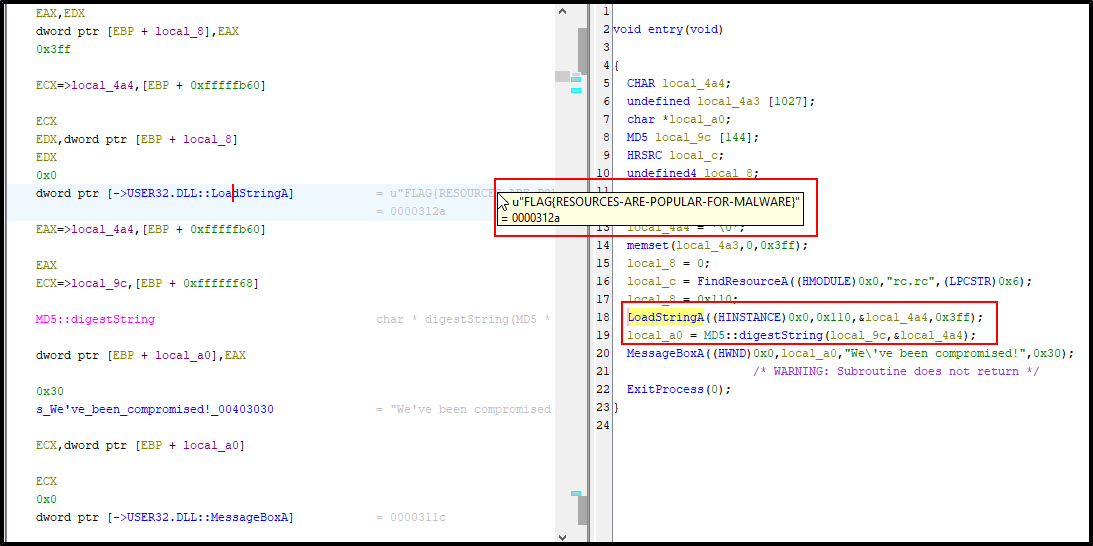
Looking at the decompiler, we can view the LoadStringA function. This API is called as:
int LoadStringA(
[in, optional] HINSTANCE hInstance,
[in] UINT uID,
[out] LPSTR lpBuffer,
[in] int cchBufferMax
);
For more info Click Here
Understand that LPSTR is the buffer to receive the string and the loaded string on that buffer is UINT . This value as seen in the decompiler is seen to be passed on the digestString. This is the actual string that is being hashed using md5.
To verify, we can go to the pointer that is being called:
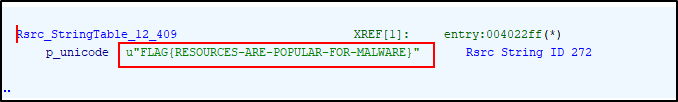
3. What is the flag of which that MD5 gets generated?
FLAG{RESOURCES-ARE-POPULAR-FOR-MALWARE}
And this completes our lab:
